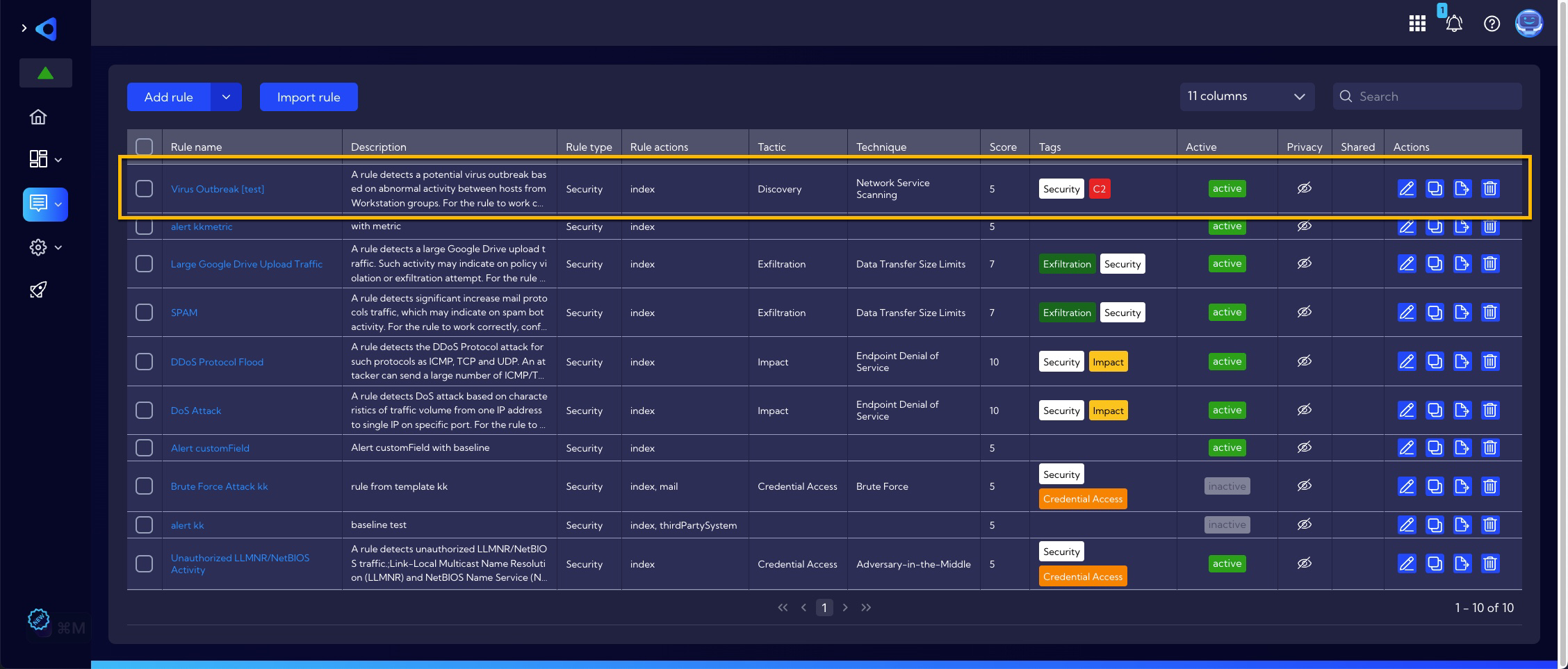
Examples of alert rule creation - advanced way
The advanced method of creating a Rule is to design it from scratch. In our example, we will create a rule named Virus Outbreak to detect malware spreading. Detection of such a case can be realized by detecting the communication of one workstation with many others in a short period of time. So let's proceed to create such a rule from scratch.
Implementation
To design a new rule go to menu [Alerts>Rule Set] and then click New rule and select From scratch option.
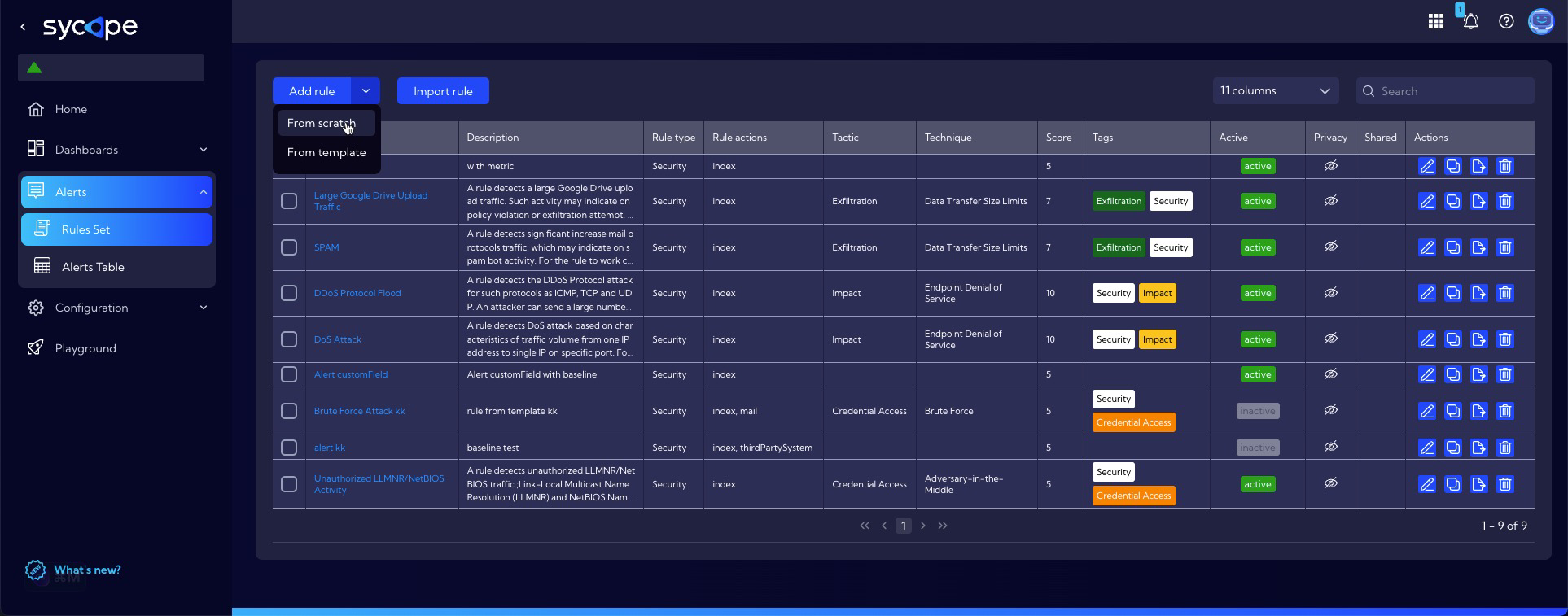
When clicked, a rule creator window appears in which the system indicates which fields should be filled in.
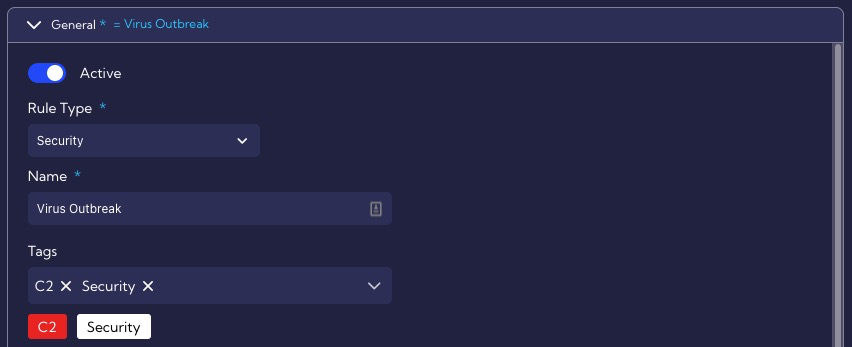
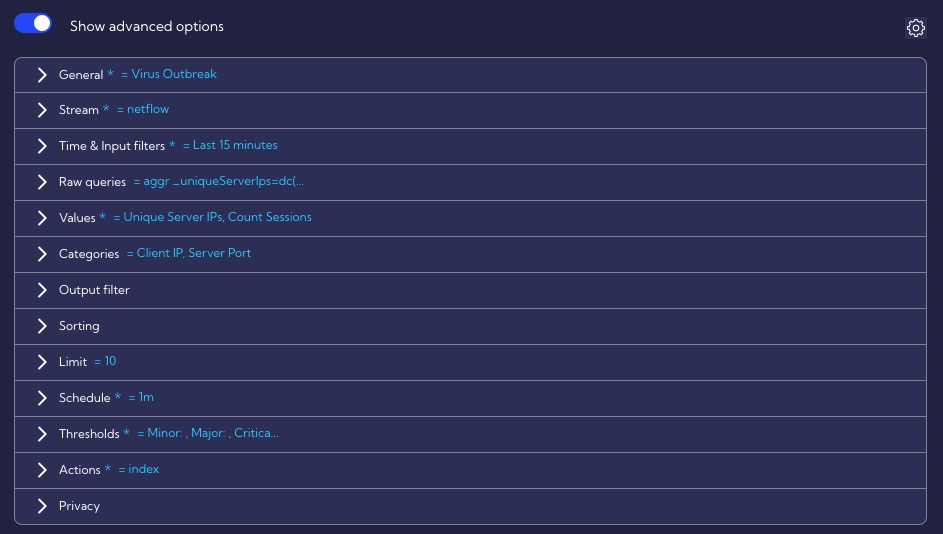
In the General section we set the rule enable (Active), fill in the required fields: Rule Type, Name, Score and optionally Tags, Description or MITRE (Tactic, Technique, Subtechnique).
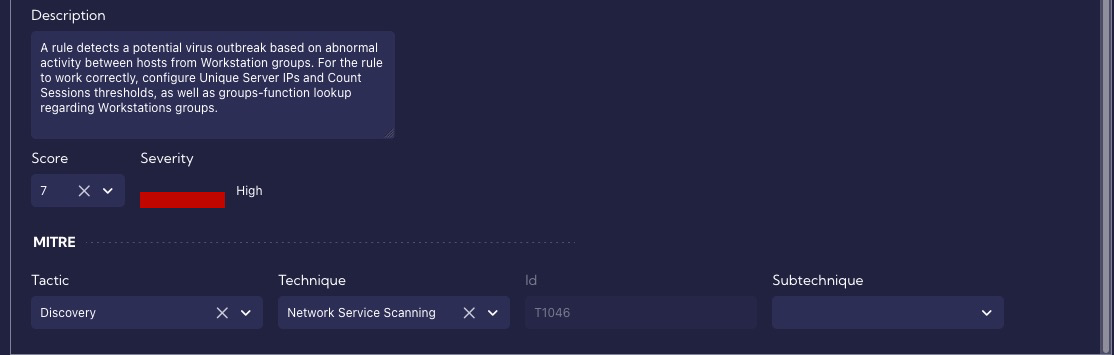
In the Stream section, we choose Netflow because we want to analyze traffic on raw flows.
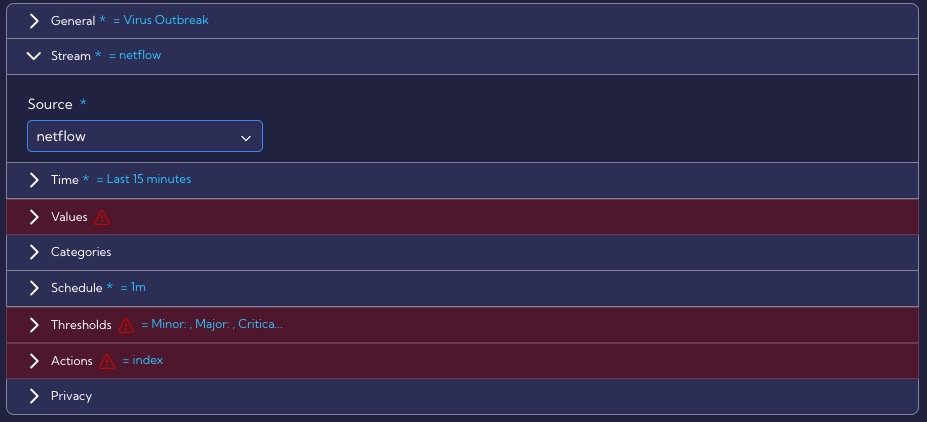
In the Time section, we leave the default value of 15 minute.
In the Values section, we select the fields for which we want to set thresholds for anomaly detection. In our case these are: Unique Server IPs and Count Sessions.
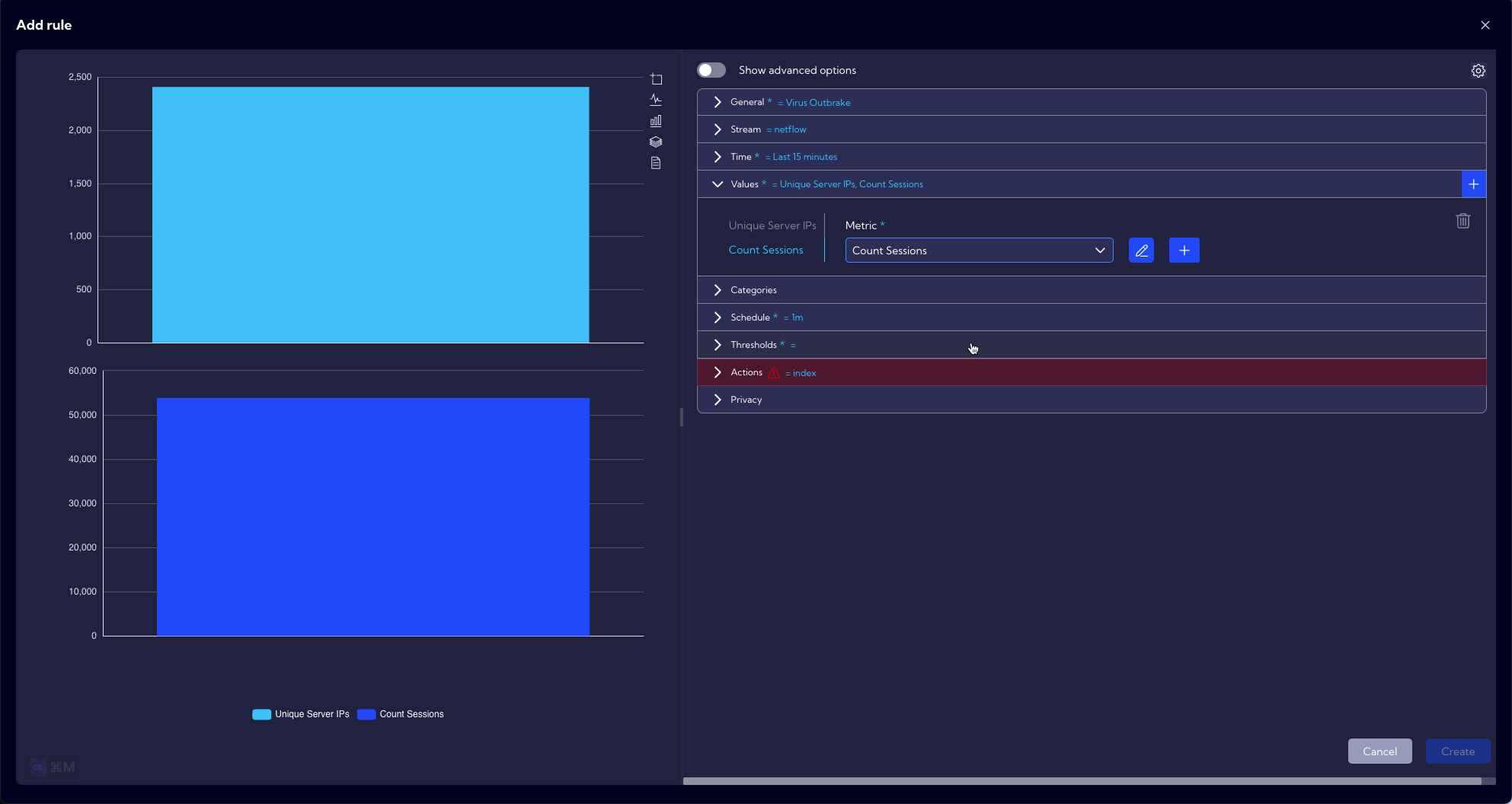 These metrics are predefined, and you can preview it in [Settings > Configuration > Objects > Metrics].
These metrics are predefined, and you can preview it in [Settings > Configuration > Objects > Metrics].
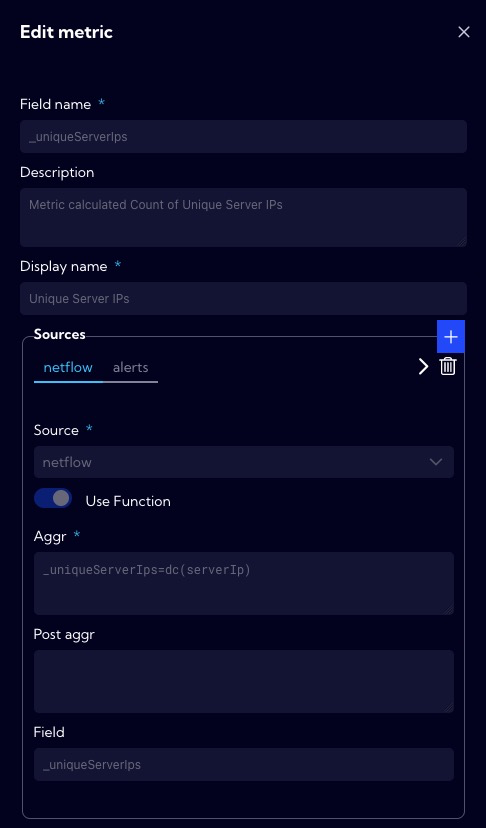
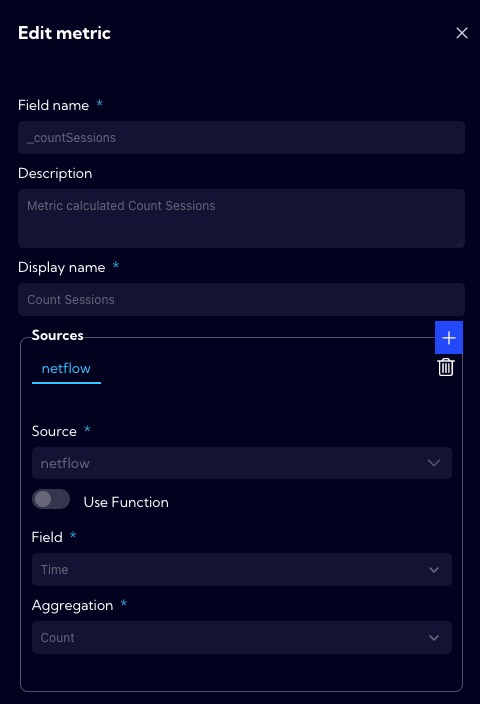
In case you want to use a custom metric, you can create one from the [Values -> Add new metric], or you can go to [Settings > Configuration > Objects > Metrics].
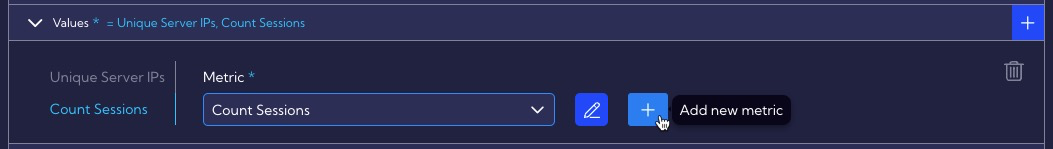
In the Categories section, we set grouping by Client IP and Server Port, because we want to detect a situation where an infected host (Client IP) communicates with multiple servers (Unique Server IPs) on a given port (Server Port).
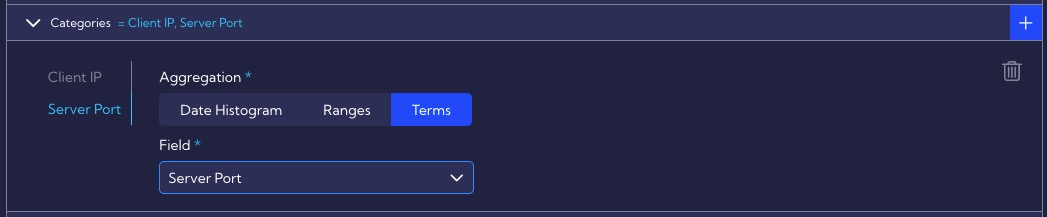
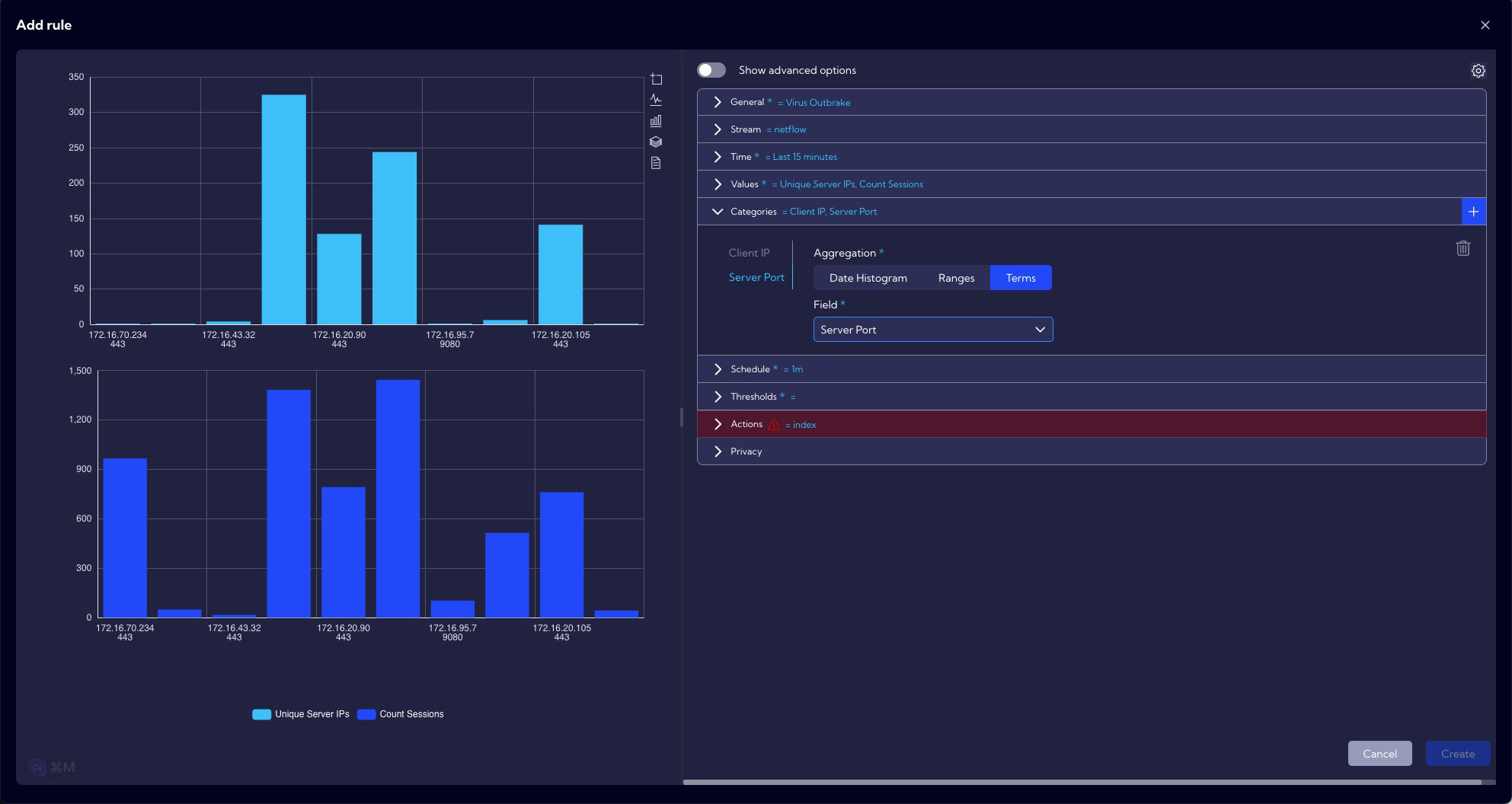
In the Schedule section, we leave the default parameters for interval and throttling, i.e. 1 minute, because, for this scenario, a time interval of 1 minute will be right. In the Indexed fields option, the same values are set as in Categories.
In the Thresholds section, set the exceedance values for the metrics configured in the Values section.
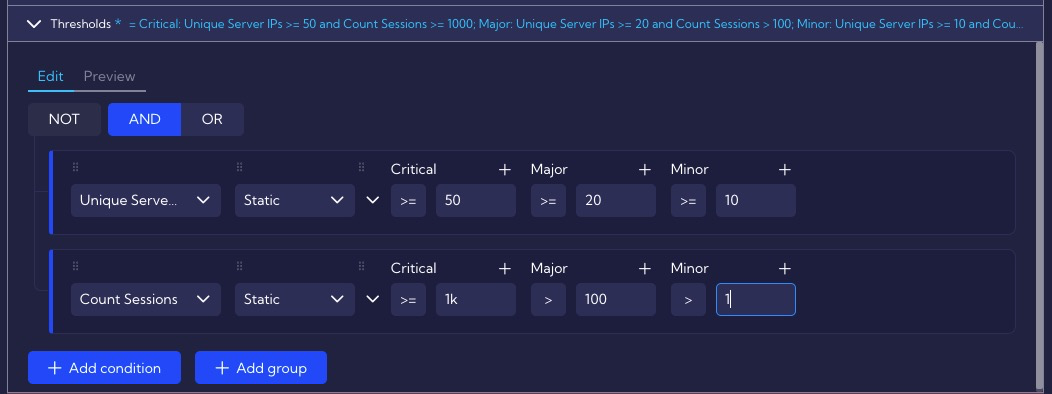
The correlation rule will trigger when in a period of 1 minute, one host (Client IP) will communicate with at least 10 hosts (Server IP) using the same port and there will be at least 1 established session (Count Sessions). If there are more of these attempts then the rule will have a higher criticality - depending on the configured thresholds (Major and Critical).
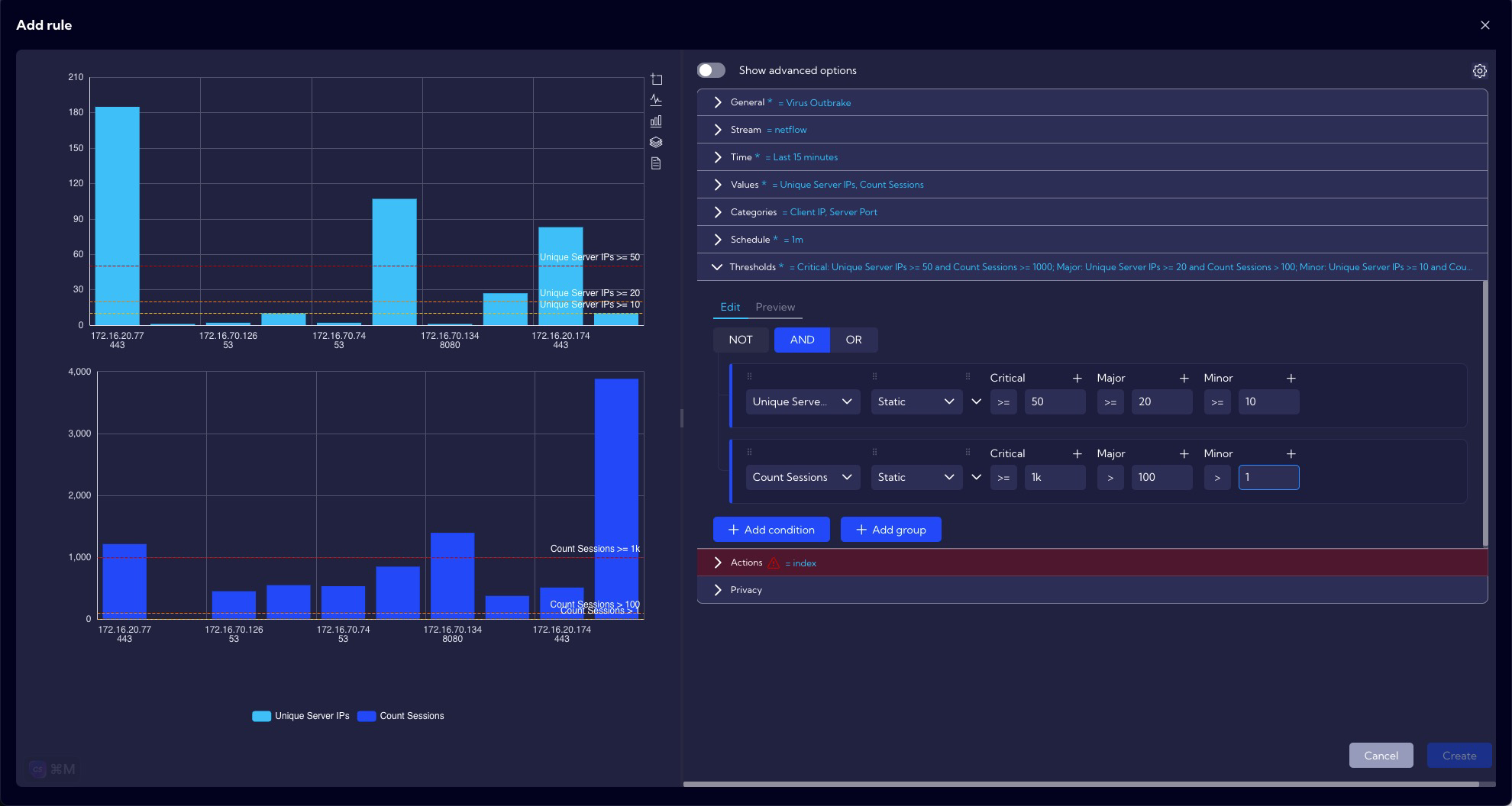
7.a.
Thresholds can be either static or dynamic. To configure dynamic thresholds, change the threshold type from Static to Reference.
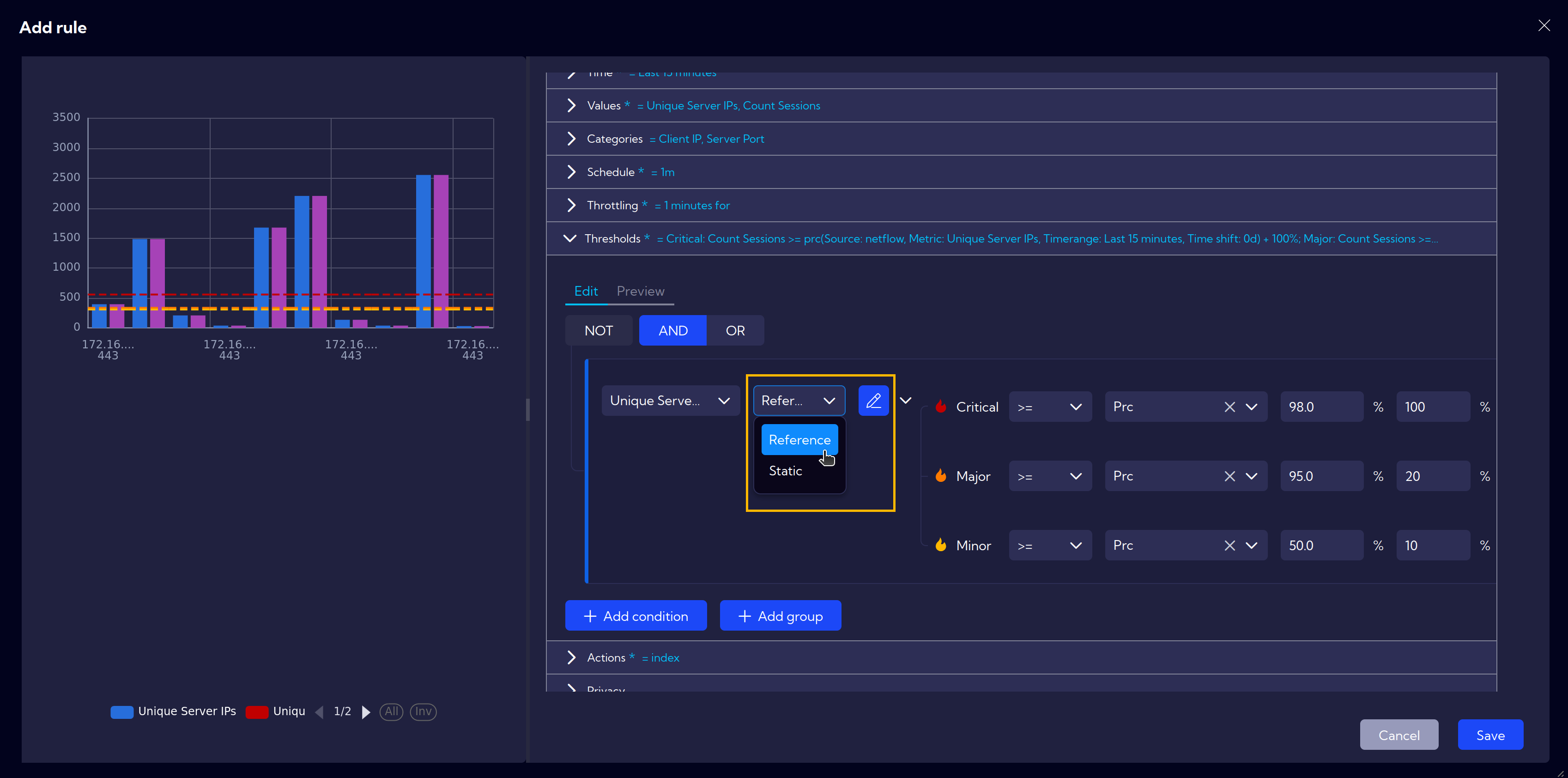
And specify the desired dynamic limits. Possible options are Avg, Max, Min, Prc and Sum.
7.b.
Additional options for setting dynamic limits are available under the Edit baseline button.
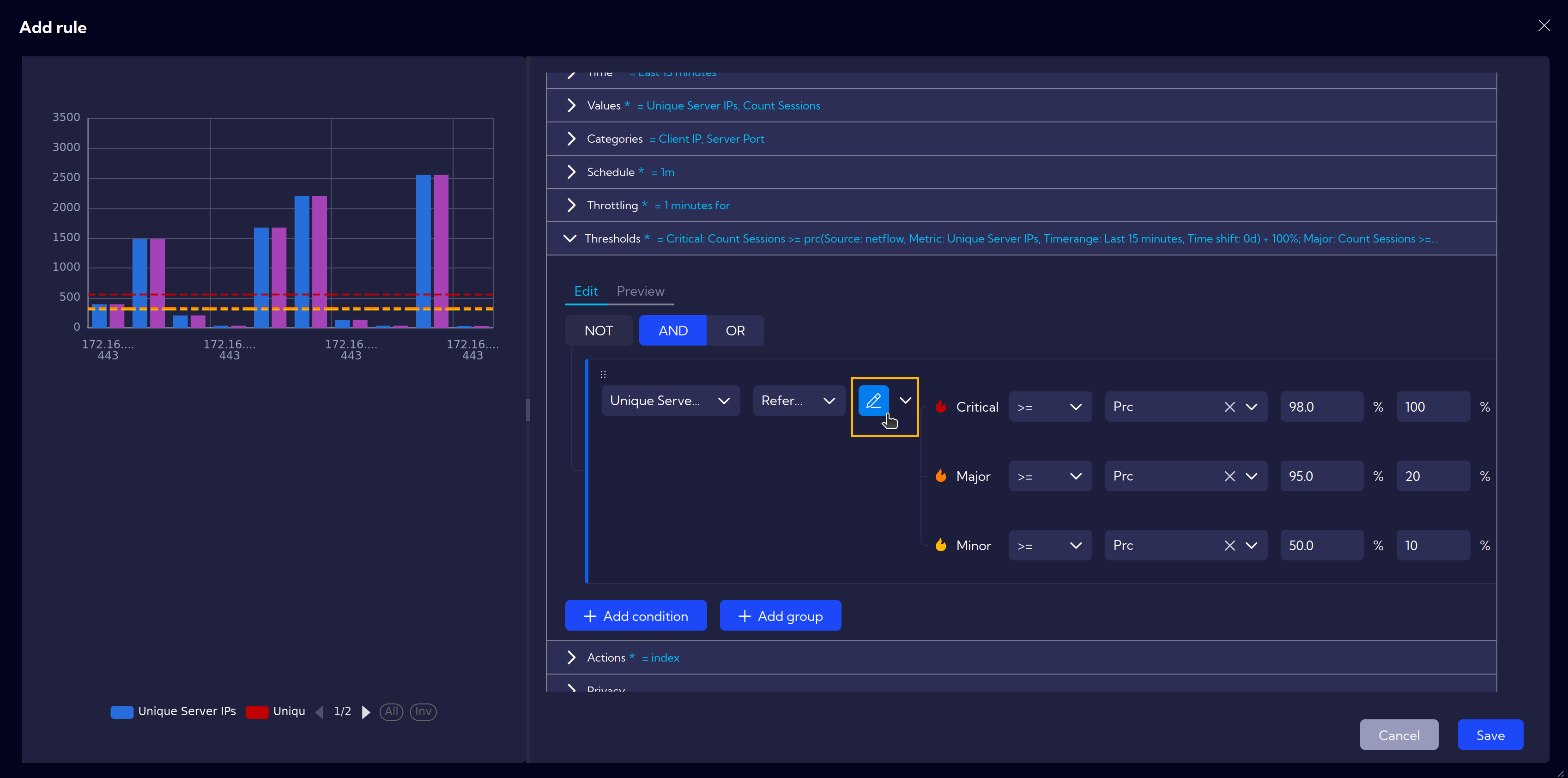
- Custom Threshold Metrics
After enabling Custom Threshold Metrics, additional data stream settings become available. These options allow you to apply extra filters and customize the data stream to meet specific requirements.
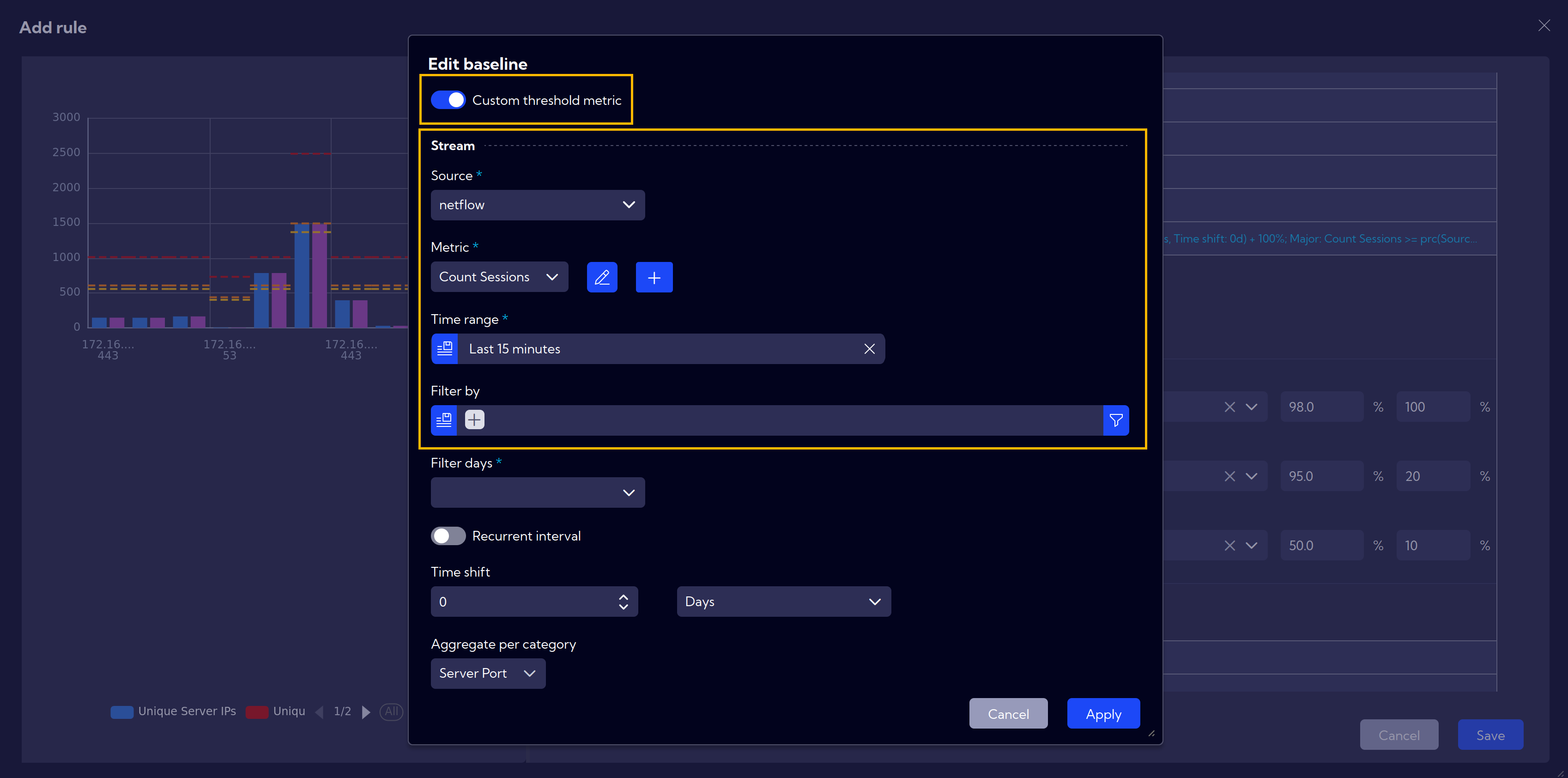
- Filter Days
The day filtering option allows for dynamically setting limits based on the day of the week, whether it is a weekday or a weekend.
The new Auto Days option automatically distinguishes between weekdays, weekends, and holidays. Based on this, it adjusts the thresholds accordingly to ensure optimal settings for each day type.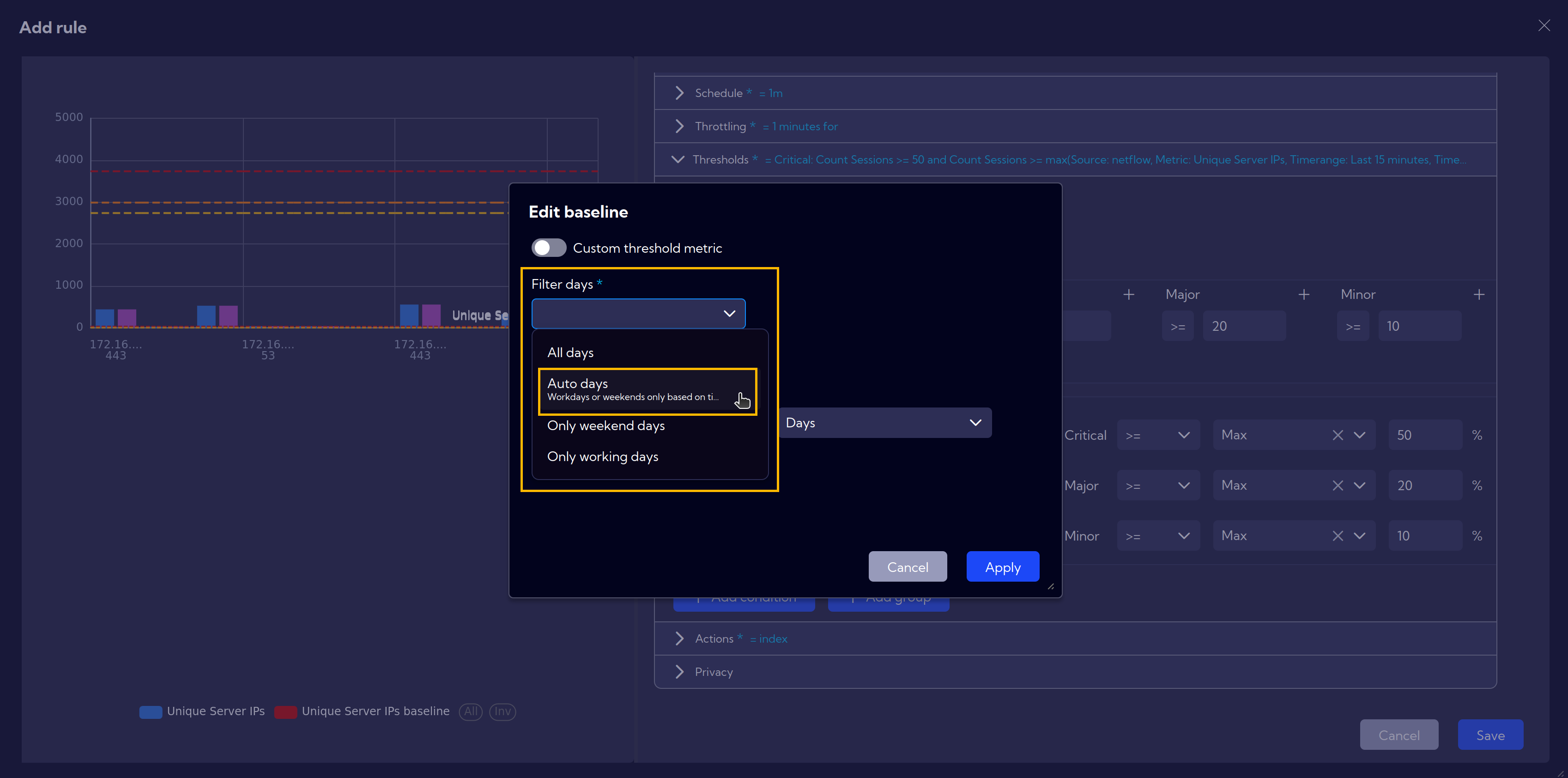
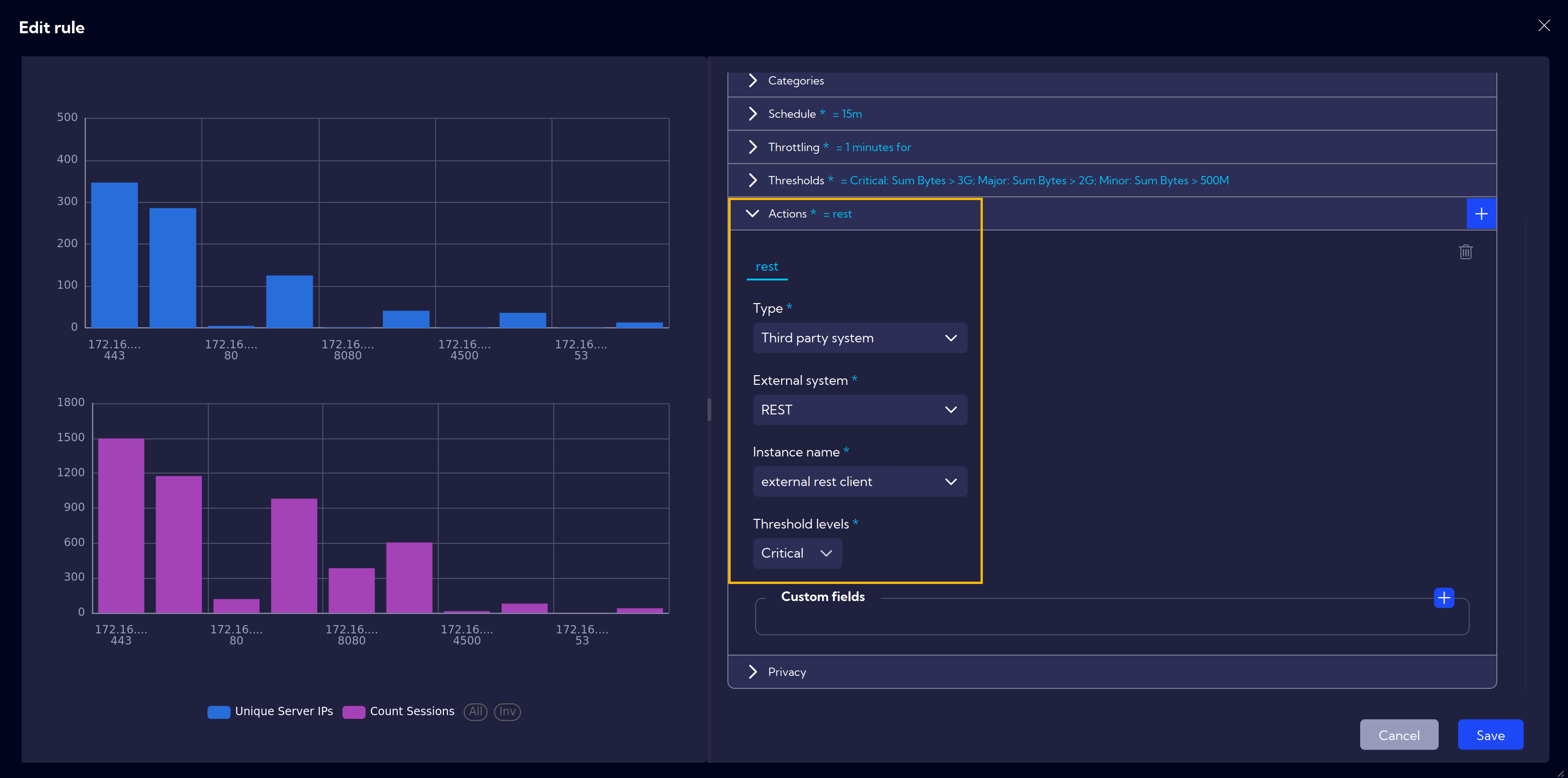
In the Actions section, we specify that all our alerts (Critical, Major, Minor) generated by this rule will be saved in the alerts table, and we also set custom fields that should additionally be included in the alert (First Client Country, First Client Function, First Client ASN).

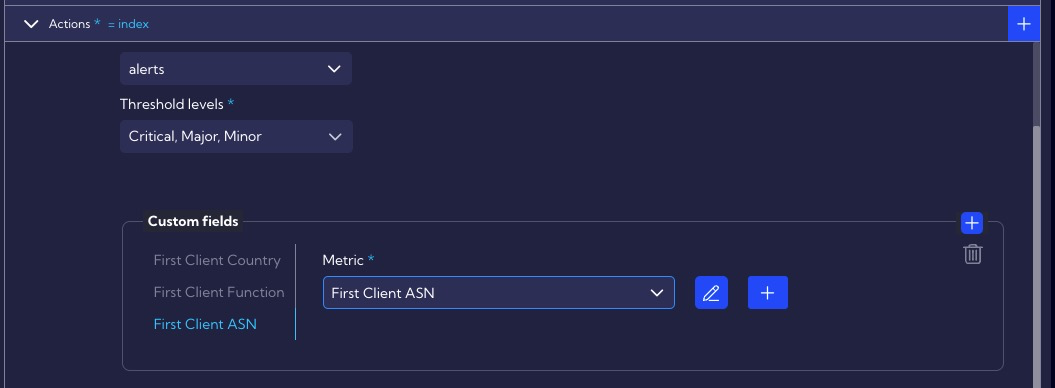
Custom fields are metrics, so their configuration is available in the [Settings > Configuration > Objects > Metrics].
8.a.
An additional option is to set up custom actions, such as sending a REST request.
Change the Type field to Third Party System.
Select REST under the External System option.
Choose the system to which the requests should be sent in the Instance name field
- the system must be previously added in [Settings > General > Integrations > External Destinations].
Choose Threshold levels that trigger the request
Once set, the system will automatically send REST requests whenever the defined threshold levels are reached.
Advanced options
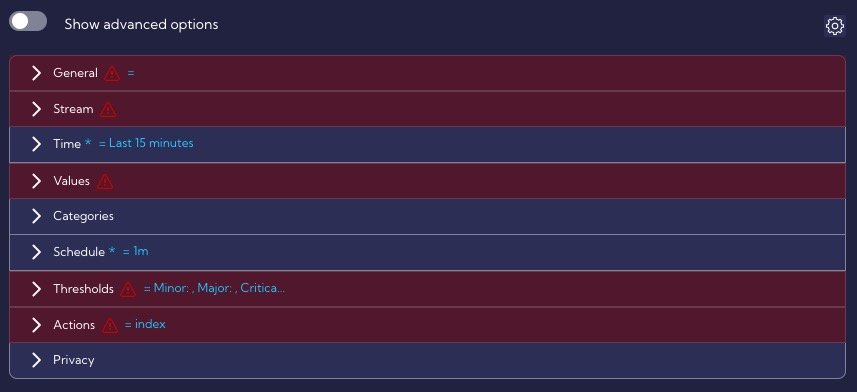
In our example, we will also use the advanced options available by clicking the Show advanced option switch.
We want our rule to generate as few False Positives alerts as possible so we use the Time & Input Filters section for this purpose.
In the Time & Input Filters section, in order to limit detection to only private addresses and the Workstations function group, we enter the following condition in the Filter by:
lookupKeyExists("groups-private", {"cidr": serverIp } ) AND lookupKeyExists("groups-private", {"cidr": clientIp } ) AND any(serverGroups, ["Workstations"])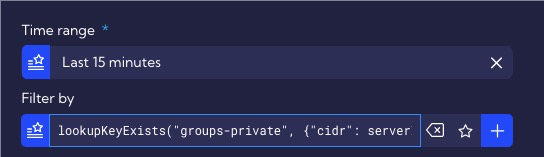
IP Addresses of the Workstations function group may be changed in the [Settings > Configuration > Mapping > Lookups].
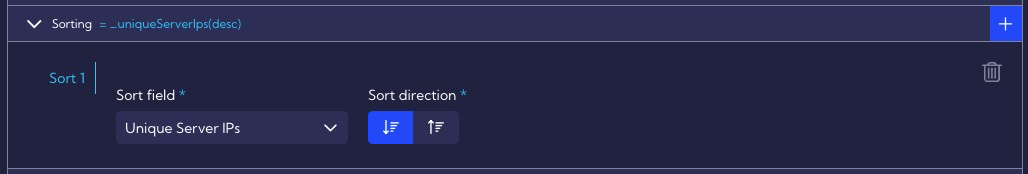
Finally, in the Sorting section, we can set sorting by some metric, such as Unique Server IPs.
If we think that our rule has been configured as we expected, we should press Create and the rule will appear in the list of rules in the system.